🧵 1/10 $K Hack Recap & Recovery Plan
The last 72 h were brutal. A sophisticated proxy exploit let an attacker mint unlimited $K on Arbitrum, drain our Uniswap pool + Morpho vault, and nuked the price with millions of fake tokens.
Here’s the recap & path forward 🧵
2/10 What happened
• Hidden “hacker-proxy” inside the ERC-1967 proxy 🚩
• Attacker flipped the pointer, seized owner() + minted at will
• Drained $1.55 M liquidity & USDC in minutes
• Price collapsed >95 % 💥
3/10 What didn’t happen
✅ Kinto L2 contracts, bridge, wallet SDK, AA infra ⛩️
✅ User deposits/withdrawals on Kinto
The bug was quite complex and relied in the 10-year-old ERC-20 proxy & Block Explorers slot mishap that we didn’t write.
4/10 Timeline (UTC)
• Jul 9 20:17 – Exploit disclosed
• Jul 10 08:40 – Attacker mints & drains liquidity
• Jul 10 09:50 – First Announcement by Kinto team
• Jul 10 16:18 – Venn disclosure recognizing Kinto was not notified
• Jul 10 21:44 – Full thread recapping the situation
• Jul 11 – ZeroShadow engagement signed & contacted authorities
• Jul 12 – Deep technical dive by @pcaversaccio
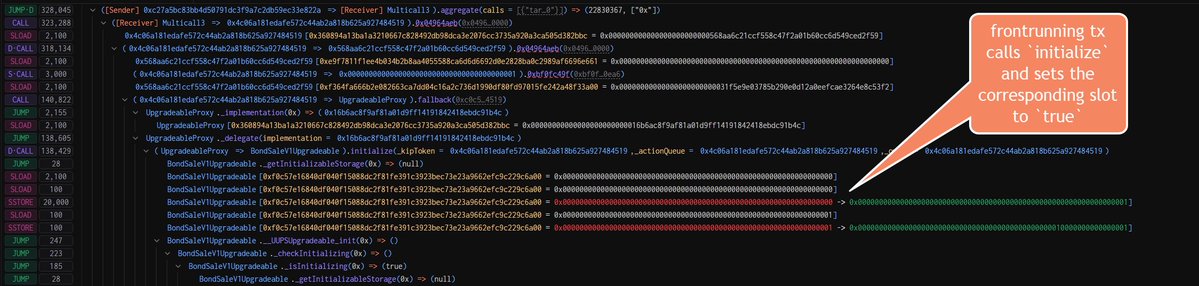
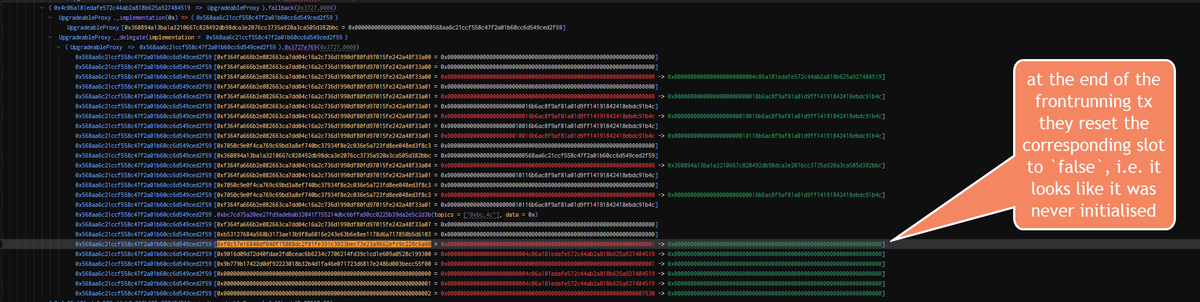
so I found out that it's even fancier. I observed that the frontrunning tx (by the attackers) calls `initialize` and protocols also call _successfully_ `initialize` after (thus they think everything is normal). But wait, how is this even possible? I had to look very deep into the storage slot changes and guess what I found: they _reset_ the `_initialized` storage slot value at the end of the frontrunning tx (after they swapped to the malicious implementation contract). This means that the proxy storage looks now as it was never initialised.
The relevant storage slot to look at is `keccak256(abi.encode(uint256(keccak256(" - 1)) & ~bytes32(uint256(0xff))` = `0xf0c57e16840df040f15088dc2f81fe391c3923bec73e23a9662efc9c229c6a00`
This is next-level evil.
5/10 Impact
• Direct loss: $1.55 M
• Market cap: –$10 M
• Morpho suppliers owed $3.2 M; borrowers hold $2.4 M (liq ≥ $3)
6/10 The comeback plan
1️⃣ Deploy proxy-less $K v2 on Arbitrum
2️⃣ Snapshot & restore ALL balances (on-chain + CEX) Block:
356170028
3️⃣ Seed new Uniswap pool & reopen CEXs at pre-hack price
4️⃣ Borrowers get 90 d to repay → suppliers recoup 85 %+
5️⃣ “Dip buyers” before our first alert receive v2 $K pro-rata
7/10 Where we are now
• Trading frozen on Gate, MEXC, BingX
• Remaining liquidity removed to protect users from trading
• Working with investigators & exchanges
• Working on the migration plan
8/10 We’re raising a recovery fund
Bootstrapping fresh liquidity isn’t free. If you believe in Kinto’s mission—safer, compliant DeFi—consider helping. Every wei goes to liquidity & restitution.
Please reach out 🙏
9/10 Our promise
This wasn’t a bug in Kinto code, but responsibility is ours. We’ll:
• Migrate the token as fast as we can 🛡️
• Keep comms 100 % transparent
• Make every affected user whole as quickly as humanly possible
26.99K
145
The content on this page is provided by third parties. Unless otherwise stated, OKX TR is not the author of the cited article(s) and does not claim any copyright in the materials. The content is provided for informational purposes only and does not represent the views of OKX TR. It is not intended to be an endorsement of any kind and should not be considered investment advice or a solicitation to buy or sell digital assets. To the extent generative AI is utilized to provide summaries or other information, such AI generated content may be inaccurate or inconsistent. Please read the linked article for more details and information. OKX TR is not responsible for content hosted on third party sites. Digital asset holdings, including stablecoins and NFTs, involve a high degree of risk and can fluctuate greatly. You should carefully consider whether trading or holding digital assets is suitable for you in light of your financial condition.




